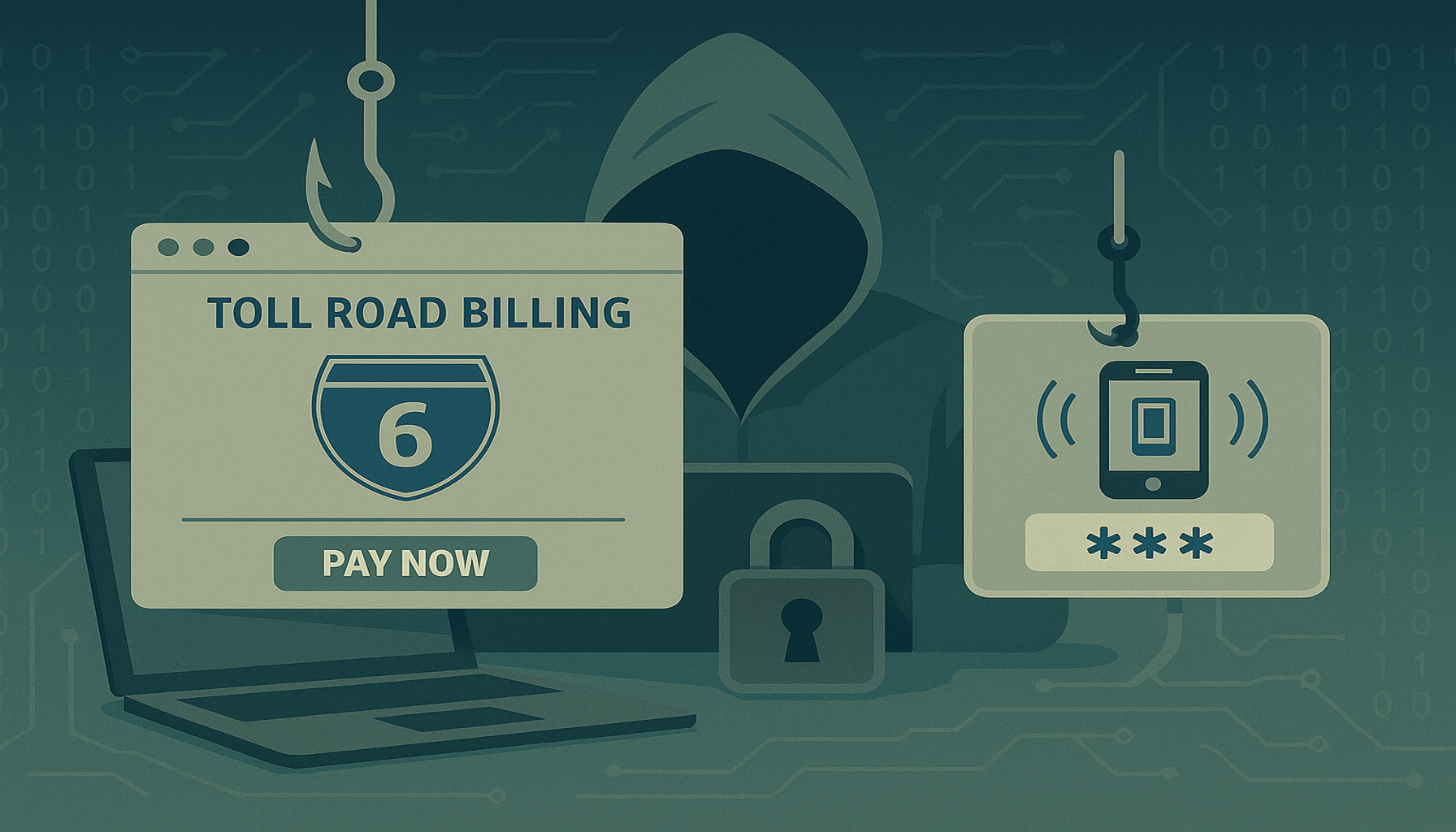
Link-Shield recently uncovered a phishing campaign that was as sneaky as it was effective — and it all started with a toll road.
Imagine this: you're driving peacefully down Kvish 6, Israel’s major toll highway. A few days later, a text arrives: “⚠️ You have an unpaid toll. Click to pay now.” The link looks convincing, the amount is low, and you click. That’s where the ride begins — straight into a phishing trap.
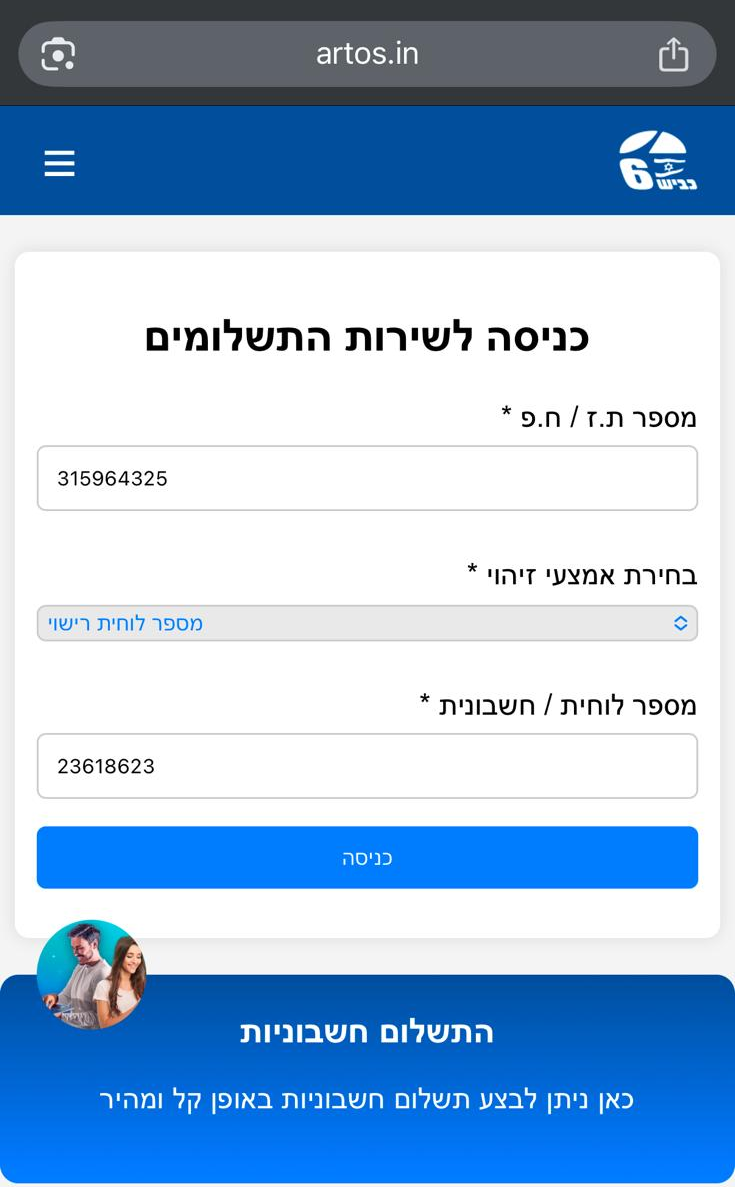
🚧 Step 1: The Fake Entrance Gate
The first page asks you to enter your Teudat Zehut (ID number) and license plate. Harmless? Not really. This is how the attackers personalize the journey.
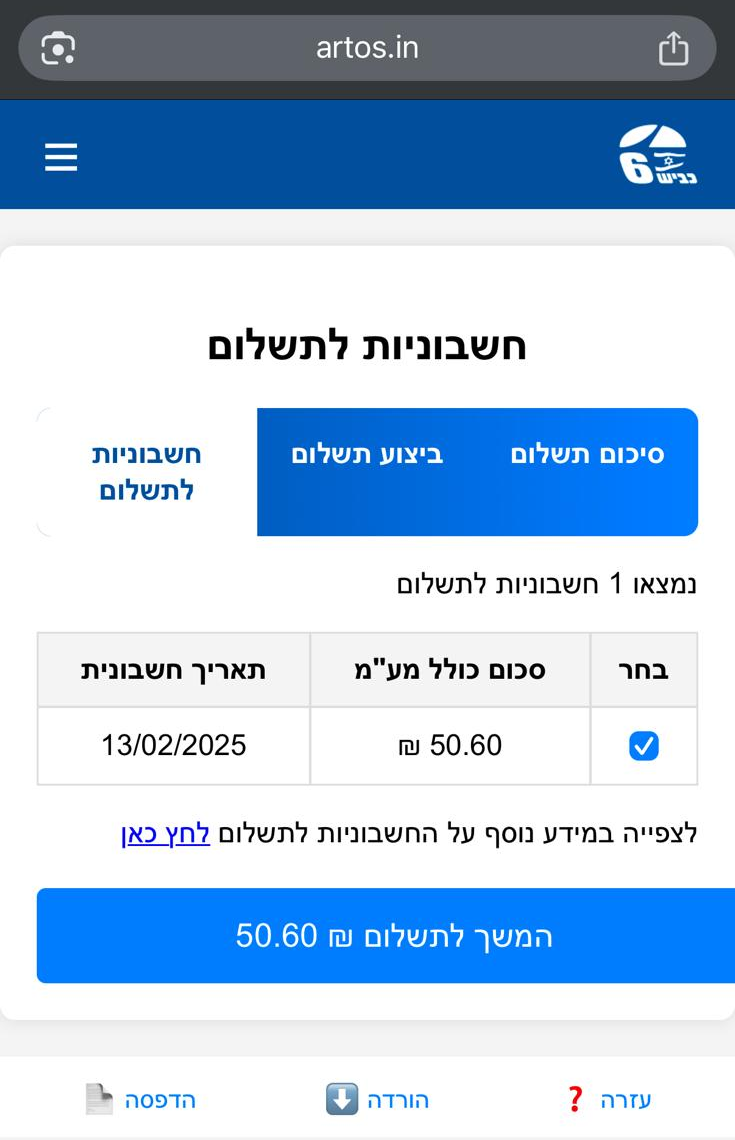
💸 Step 2: The Toll Bill You Never Owed
Next up: a believable-looking payment screen showing a small charge. Small enough that most users wouldn’t think twice. The perfect bait.
💳 Step 3: The Real Pay Day — for the Attackers
Users are then prompted to enter their full credit card details, ID, and phone number. This is where the attack collects its jackpot.
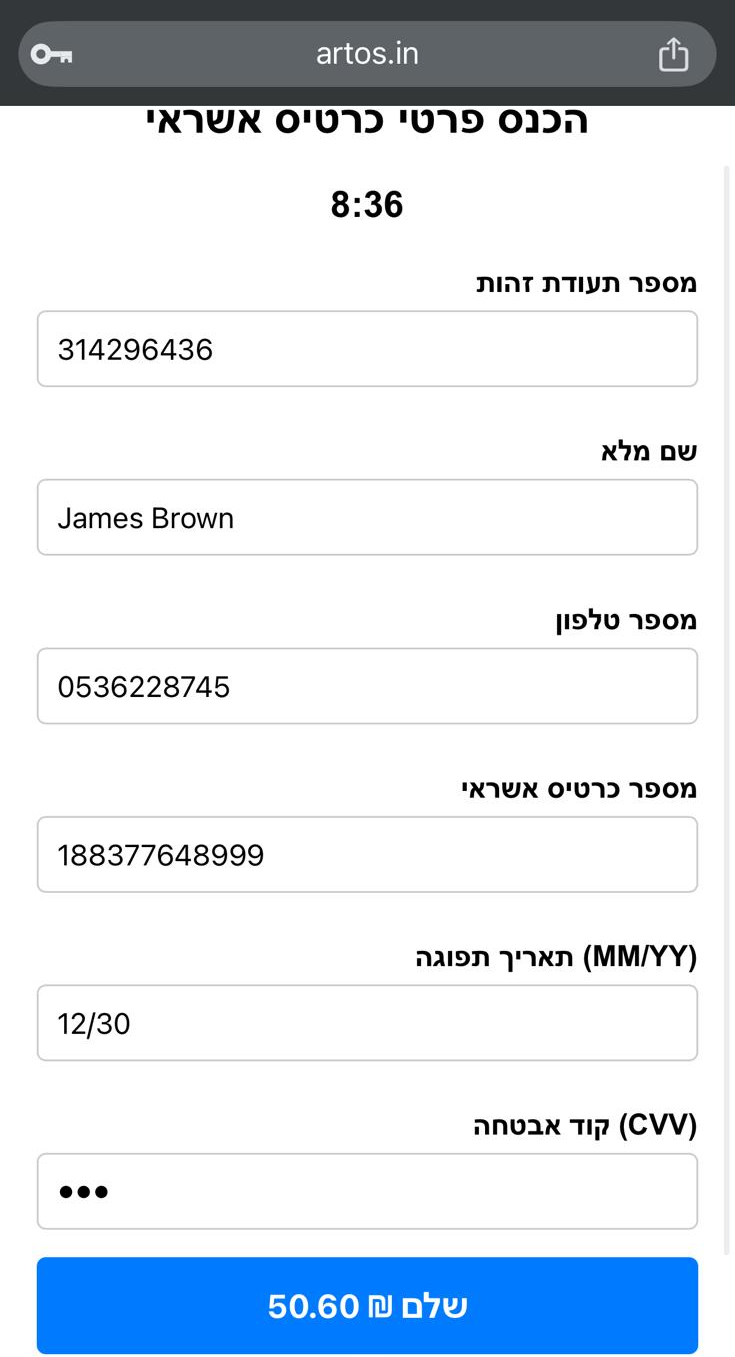
🔐 Step 4: 2FA Stolen in Real Time
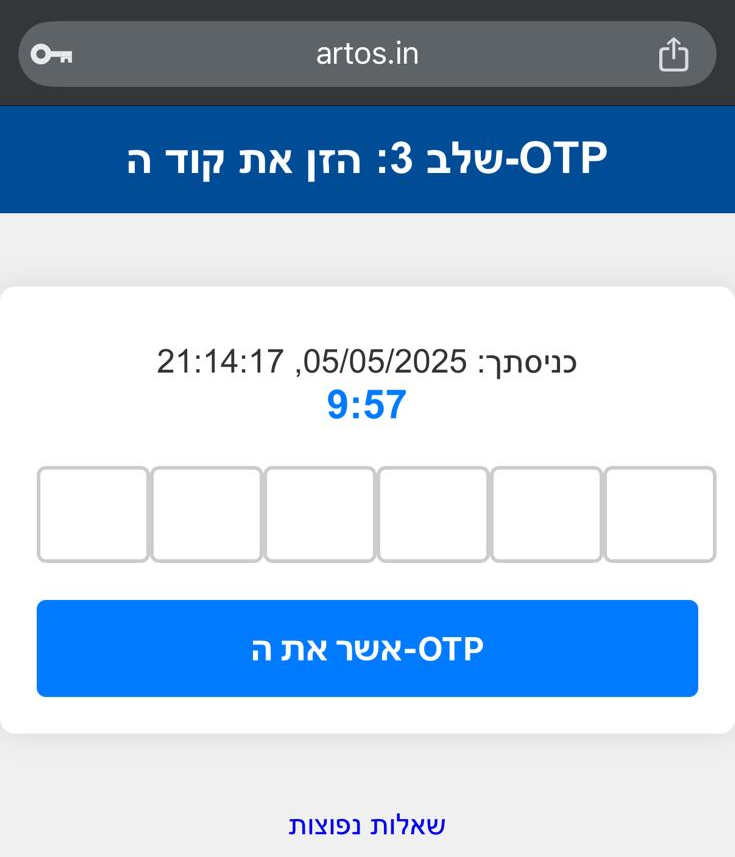
The final trick: a prompt for your 2FA code — likely sent via SMS. Once entered, the user is redirected to the real Kvish 6 website, making everything feel legitimate.
🧠 Why This Worked
- The amounts were small and believable.
- The campaign looked localized and legitimate.
- 2FA codes were phished in real time — allowing attackers to complete transactions instantly.
🛡️ How Link-Shield Caught It
Thanks to our real-time phishing detection engine, Link-Shield identified and blocked the campaign early. Users were protected before their data reached the wrong hands.
We also coordinated with national CERT teams to take down the malicious infrastructure and prevent further damage.
🚀 Takeaway
Phishing campaigns are getting more local, more polished, and more urgent-looking. Link-Shield continues to adapt — so you don’t have to second-guess every toll notice or login request.